Which of the Following Is Used for Biometric Authentication
Gait Signature Voice Recognition and Facial Recognition are physiological biometric that could be used for authentication. A single characteristic or multiple characteristics could be used.
Biometric Authentication Methods Fingerprints Facial Recognition Hand By Anh T Dang Towards Data Science
A retinal scan will illuminate the complex blood vessels in a persons eye using infrared light making them more visible than the surrounding tissue.

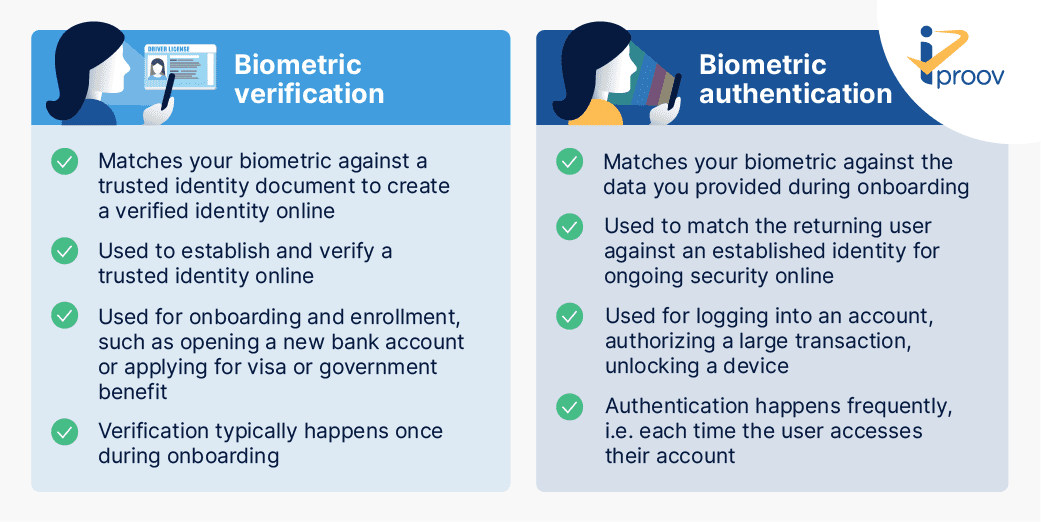
. The following biometric identification and authentication devices are available and can be further explained during a face-to-face consult with The Intelligence Group. Benefits of biometric authentication. The following strategies can help to minimize the risks associated with the use of biometric data.
Truly this technology is rooted in our biology. March 14 2022. Facial recognition is a very well-known form of biometric authentication popularized in the many spy dramas and sci-fi tales in popular media.
Answered Apr 2 by sharadyadav1986. It is also used to identify individuals in groups that are under surveillance. Cognitive biometrics is considered to be much easier for the user to remember because it is based on the users life experiences.
Apples introduction of Touch ID in 2013 has paved the way for fingerprint- face- and iris-recognition technology to leave the almost exclusive domain of law enforcement. Fingerprints Hand topology side view or geometry top-down view Palm scans Retina scans Iris scans Facial scans Voice recognition. Biometric authentication is a growing part of the tech landscape its in our schools offices airports government buildings and more recently in our smartphones.
Match each of the following terms to its meaningIpacket filteringIIIP addressIIIfirewallIVCAPTCHAVbiometric authentication deviceAprogram that generates distorted text and requires that it be typed into a boxBreads a unique personal characteristic and converts its pattern to a digital codeChardware or software for protecting computers from. Biometric has been for long the target of future authentication that expected that biometric authentication will largely displace other means of our current authentication and access control. All of the following are used for authentication except.
Biometric authentication or realistic authentication is used in computer science as a form of identification and access control. Huawei products request a password every three days if biometric unlocking is enabled. E All the options.
A cognitive password is a fact or opinion-based password extracted from that persons life experience. Digital signatures O certificates of authority. Biometric Authentication Certificate-based Authentication Certificate Pinning Credential Transmission Scoping Domain Trust Policy Multi-factor Authentication One-time Password Strong Password Policy User Account Permissions Message Hardening Message Authentication Message Encryption Transfer Agent Authentication Platform Hardening.
We use facial recognition every day to identify our friends and families and distinguish strangers. Biometric identifiers are the distinctive measurable characteristics used to label and describe. Cognitive biometrics is also called knowledge-based authentication.
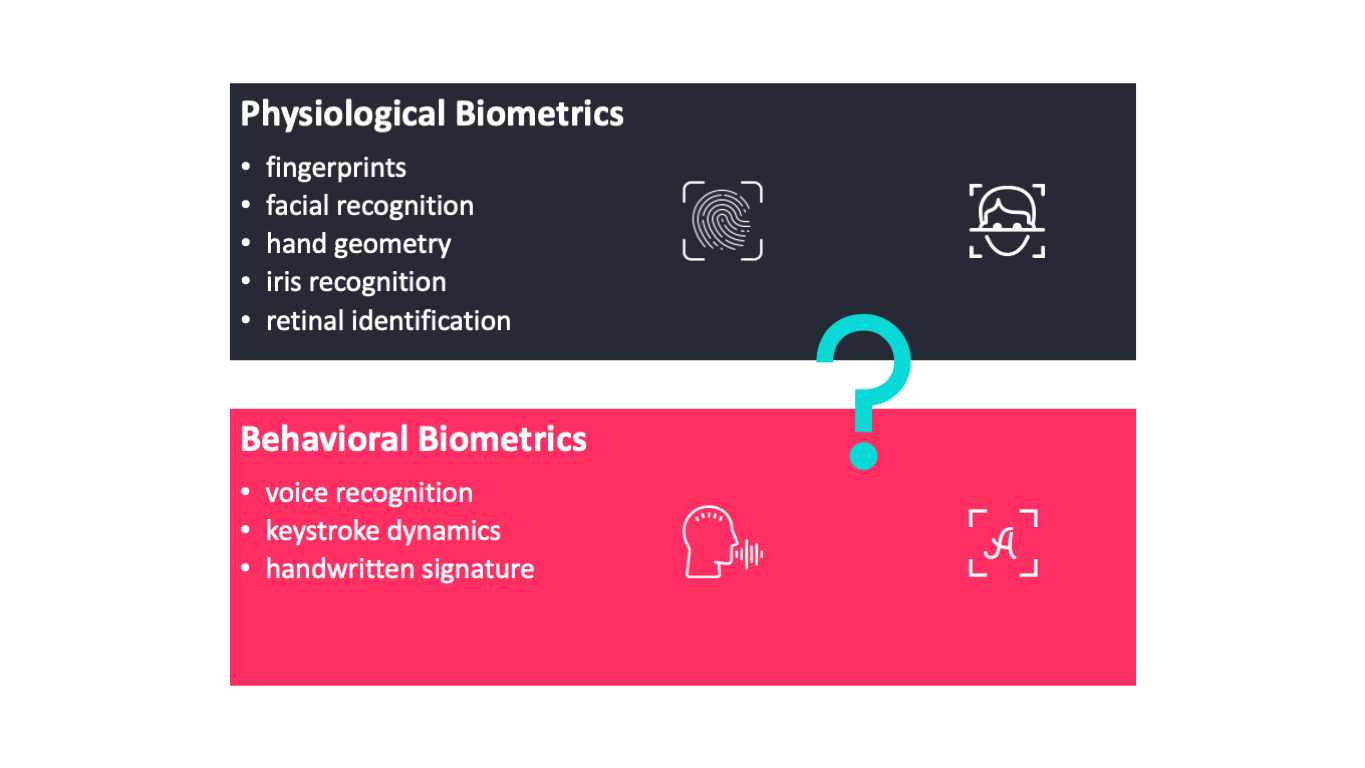
Common attributes used for biometric systems include. Fingerprints facial recognition hand geometry iris recognition retinal identification voice recognition keystroke dynamics and handwritten signature. This also makes it more difficult for an attacker to imitate.
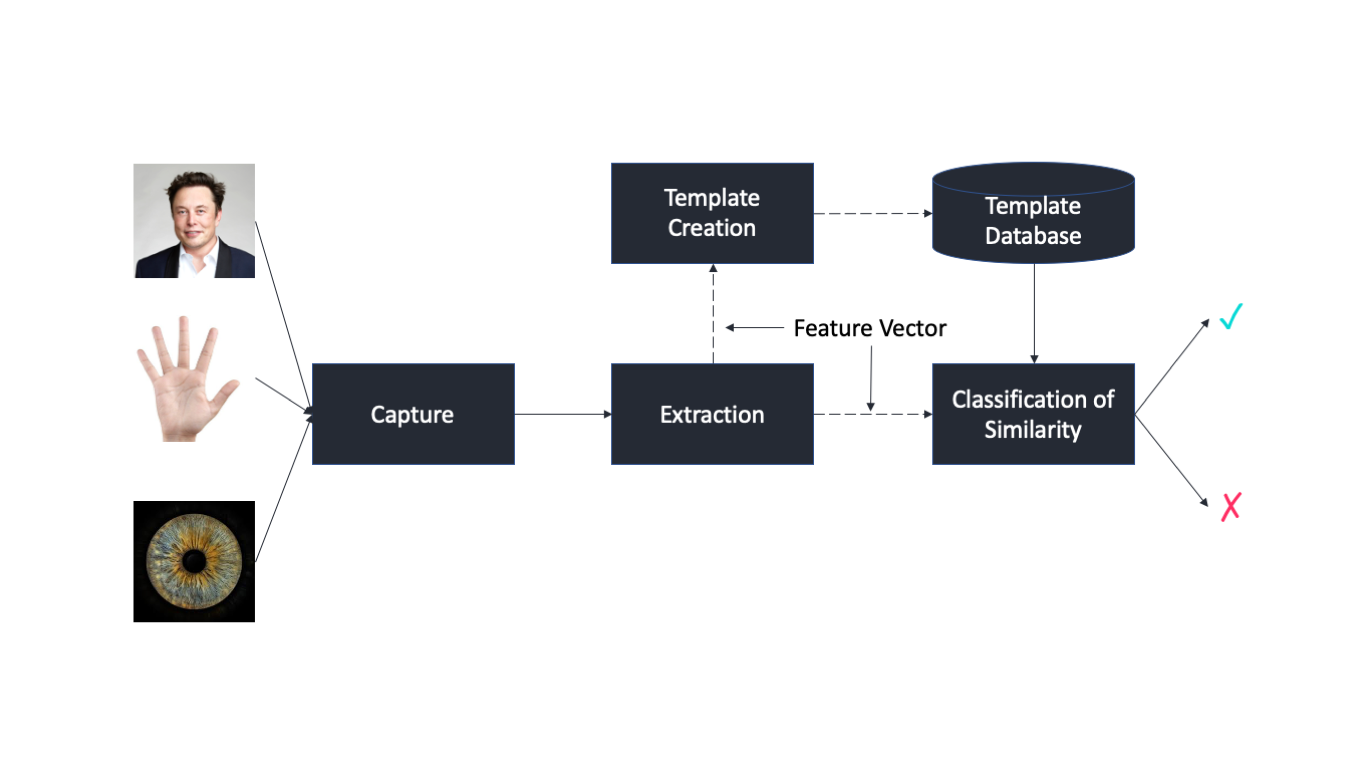
28 Which of the following is used for biometric authentication. Biometric authentication methods The following technologies can be used to digitally identify people or grant them permission to access a system. This could be a fingerprint an iris scan a retina scan or some other physical characteristic.
E-banking applications use biometric authentication after the customer has logged in thus simply adding an extra layer of security to the whole process. Biometric authentication involves using some part of your physical makeup to authenticate you. A smart cards B facial features C passwords D personal identification numbers Answer.
Chemical biometric devices DNA deoxyribonucleic acid matching uses genetic material to. These techniques are based on the physical characteristics of. Instead of typing a password we can just authenticate by tap the fingerprint.
Currently biometric authentication isnt used for completing financial transactions. Crossover error rate CER is the point in which Type I and Type II errors are equal and represents the most important evaluation rating for a biometric system. E All the options.
One of the best ways to authenticate and verify identity online is through biometrics. Gait Signature Voice Recognition and Facial Recognition are physiological biometric that could be. The following highlights benefits precautions and strategies for protecting data subjects and biometric data.
Biometrics authenticates an individual by a unique personal trait. Biometric authentication can now be found in almost every phone. It all depends on the infrastructure and the level of security desired.
Biometric authentication is when the users fingerprints facial patterns and voice are used to verify their identity. Answered Apr 2 by sharadyadav1986. With biometric authentication the risk of a bad actor gaining access to user systems and information decreases when used as part of a multi-factor authentication strategy.
Security researchers consider the eye as one of the most reliable body parts for biometric authentication since the retina and iris remain almost completely unchanged during a persons lifetime. Chemical biometric devices DNA deoxyribonucleic acid matching uses genetic material to identify a. Biometrics are body measurements and calculations related to human characteristics.
Based on the behavior biometric authentication techniques are categorized into two parts physiological techniques and behavioral techniques. Types of Biometrics Most people have used biometrics mostly through fingerprint or facial recognition to.
Biometric Authentication Methods Fingerprints Facial Recognition Hand By Anh T Dang Towards Data Science

What Is Biometrics Authentication Types Of Biometrics And Trends
No comments for "Which of the Following Is Used for Biometric Authentication"
Post a Comment